CyberHunter’s Security Operation Center (SOC) works for you 24x7x365. Attackers never sleep, and neither do we. Our security analysts leverage next generation SIEM technology combined with threat intelligence and behavioral analysis to monitor, analyze and detect advanced threats and suspicious activity.

CLIR Security - SOC as a Service
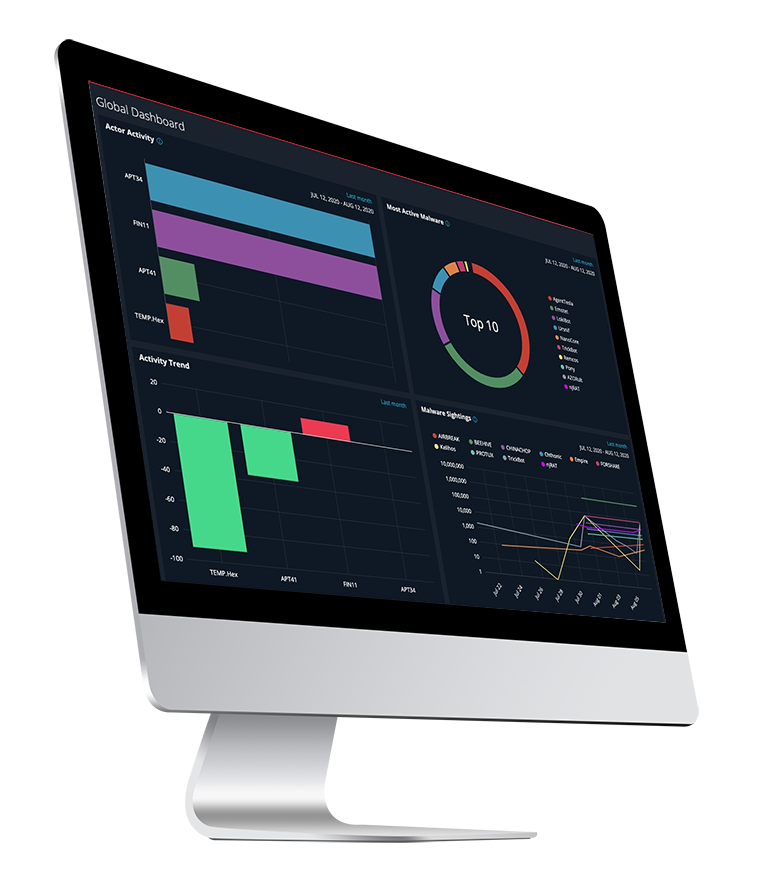
24x7x365 Threat Detection, Analysis and Alert Triage
- A Certified SOC 2 Type II, ISO 27001 Operations Center
- USA, Canada SOC locations
- No contract. No commitment. No onboarding fees.
- Predictable fixed monthly cost
- Weekly / Monthly SOC Reports
- 30 Minute GOLD SLA Response
- 90 Day Log Retention is standard
- Includes SIEM licensing
CLIR Security - SOC as a Service
Continuous Cyber Threat Hunting & Vulnerability Management
- User Behavior Analytics (UBA)
- MITRE ATT&CK Framework
- Command & Control & Botnets
- Malware/Ransomware
- Phishing/Spear Phishing Attacks
- Indicators of Compromise
- Privileged Access Monitoring
- Privilege Escalation
- Lateral Movement Attacks
- Impossible Travel
- Unauthorized Access
- Brute Force Attacks
- VPN Access Anomalies
- Policy Violation & Misconfigs
- Suspicious Activities
- Defense Evasion
- Data Exfiltration
- DoS/DDoS
How SOC Detection Works
Security Devices
Security Devices
Servers & Mainframes
Network & Virtual Activity
Data Activity
Application Activity
Configuration Information
Vulnerabilities & Threats
Users & Identities
CORRELATION
- Logs/events
- Flows
- IP Reputation
- Geographic Location
ACTIVITY BASELINING & ANOMALY DETECTION
- Logs/events
- Flows
- IP Reputation
- Geographic Location
OFFENSE IDENTIFICATION
- Credibility
- Severity
- Relevance
